HTTP/2 can significantly improve your website’s page speed because it allows browsers to simultaneously process multiple requests over the same connection. In this article, learn how you can easily improve your site’s load speed with HTTP/2.
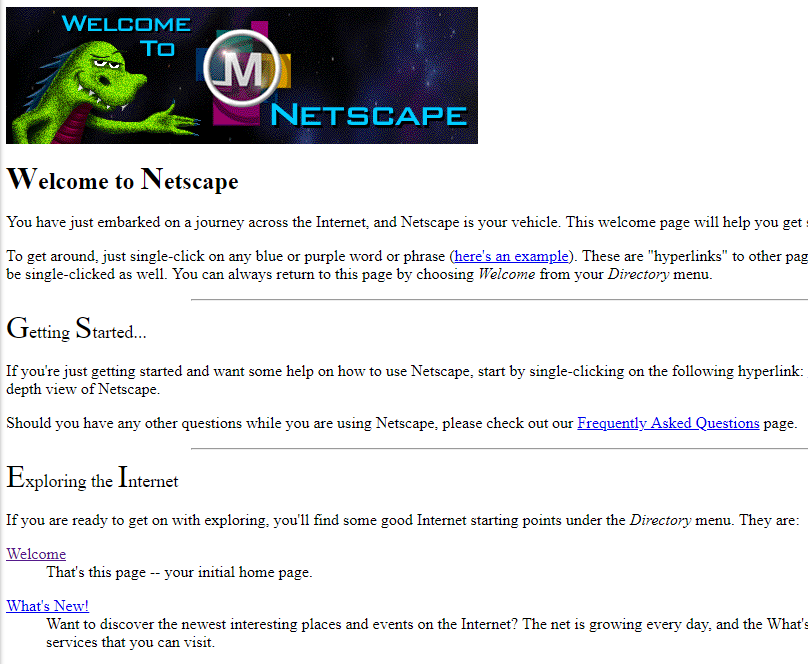
..When HTTP was first created, this wasn’t such a big deal. Back then, webpages tended to look like this:
Figure 1: Websites in the age of HTTP/1
That entire webpage consists of two files: the HTML webpage and a single image banner. With dial-up internet speeds being the fastest thing available, website creators couldn’t get very fancy. But with only two files, being limited to downloading one file at a time wasn’t a problem.
Today’s webpages are far more complex. For example:
- The homepage of amazon.com requires 315 separate requests/files.
- The homepage of cnn.com triggers 521 separate requests for files.
- The homepage of ebay.com makes 256 separate requests.
As you can see, it would be very inefficient to download these files one at a time, or even to download 6 at a time. That’s the problem that HTTP/2 fixes.
HTTP/2 allows browsers to simultaneously download multiple files over the same connection. This makes it a lot faster for the user to download all the files needed for a given webpage.
If you’d like a simple (but detailed) explanation of how HTTP/2 works, I recommend An introduction to HTTP/2 for SEOs by Tom Anthony. It’s even got great little illustrations using trucks that help make a intangible concept super-easy to conceptualize and understand:
Ryte: Website Analysis
Improve your performance online with the Ryte suite
Monitor, analyze and optimize the key elements of your website efficiently with one tool.
GitHub’s CSP journey
We shipped subresource integrity a few months back to reduce the risk of a compromised CDN serving malicious JavaScript. That is a big win, but does not address related content injection issues that may exist on GitHub.com itself. We have been tackling this side of the problem over the past few years and thought it would be fun, and hopefully useful, to share what we have been up to.
Just to get everyone on the same page, when talking about “content injection” we are talking about:
- Cross Site Scripting (XSS) – Yup, the most common web vulnerability of the past, present, and foreseeable future. Given its prevalence, many developers are familiar with XSS and the obvious security consequences of allowing injected JavaScript to execute on your site.
- Scriptless attacks – This is a more nuanced issue and is frequently not considered since people are too busy fending off XSS. But, as has been documented by Michal Zalewski in “Postcards from the post-XSS world”, Mario Heiderich (et al) in “Scriptless Attacks –
Stealing the Pie Without Touching the Sill”, and other related work, preventing XSS does not solve all of your content injection problems.GitHub uses auto-escaping templates, code review, and static analysis to try to prevent these kinds of bugs from getting introduced in the first place, but history shows they are unavoidable. Any strategy that relies on preventing any and all content injection bugs is bound for failure and will leave your engineers, and security team, constantly fighting fires. We decided that the only practical approach is to pair prevention and detection with additional defenses that make content injection bugs much more difficult for attackers to exploit. As with most problems, there is no single magical fix, and therefore we have employed multiple techniques to help with mitigation. In this post we will focus on our ever evolving use of Content Security Policy (CSP), as it is our single most effective mitigation. We can’t wait to follow up on this blog to additionally review some of the “non-traditional” approaches we have taken to further mitigate content injection.
Report URI: Content Security Policy, powerful monitoring and protection
With Content Security Policy, and reporting provided by Report URI, you can take full control of resources that are permitted to load on your site. Taking control of where JavaScript can be loaded and executed from is a powerful mitigation for one of the most common forms of attacks seen against web applications, Cross-Site Scripting (XSS).
KEY FEATURES
Whilst the main attraction to CSP is mitigating Cross-Site Scripting attacks, it has a lot more to offer. Here are just a few of the things that you can do with CSP:
- Detect mixed-content
- Control where forms can post data
- Restrict loading of any content type
- Automatically fix mixed-content
- Control nested browsing contexts
- Defend against click-jacking